Sniffing Philips Hue Zigbee traffic with Wireshark
I have a Philips Hue gateway at home that is connected to a number of Philips Hue lights, as well as some IKEA trådfri light bulbs, and a couple of OSRAM Lightify light strips. Most of the time the network works quite well, but some of the time a few of the lights become unreachable. I read a rumor online that the Hue lights and the other lights are actually on two different Zigbee networks. Of course, if only I had a way of sniffing the Zigbee traffic I could diagnose these problems. And thus began this quest.

I started by buying a Zigbee sniffer, I found that the Texas Instruments CC2531 chip is widely used, and available in a cheap USB package. I purchased this USB CC2531 Zigbee sniffer, but others are probably equally good. After the dongle arrived I spent quite a while thinking that I need to replace the stock firmware, because of various old projects on GitHub (Sensniff, ccsniffpiper, etc.). Fortunately, you do not need to change the stock firmware. The best software package seems to be KillerBee which supports both sniffing and injection; however only sniffing with the CC2531. Installing KillerBee on Ubuntu is quite easy. You need to install scapy, and a few dependencies. The installation instructions are probably more up to date than this blog post.
Starting the sniffing is really easy, if you know the channel the Philips Hue is operating at. I think channel 11 is the default, but it is displayed in the Hue app, under info for the bridge:
sudo zbwireshark -c 11
This will launch a background process, and an instance of Wireshark that is monitoring the channel. At this point you can see the traffic; but everything is encrypted…
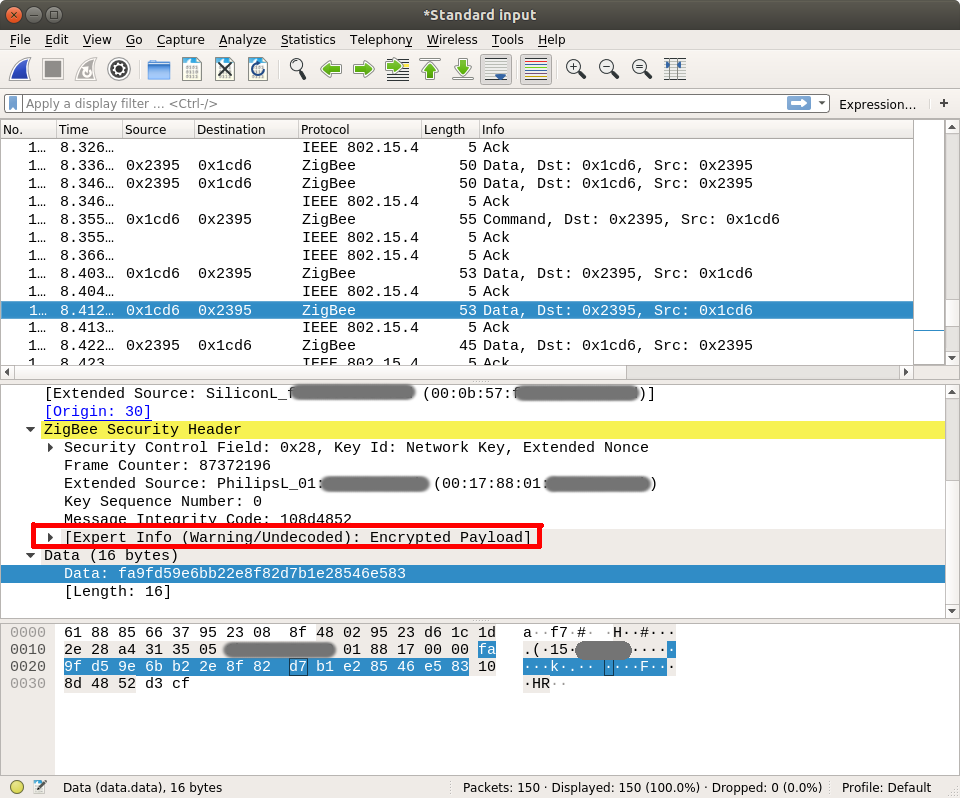
A very incomplete intro to Zigbee encryption
Zigbee traffic can be encrypted with AES-128, which is a symmetric encryption scheme. This means the key to encrypt and decrypt is the same. There is a number of keys that can be used to encrypt a single packet payload:
- The Network Key, which is unique to this Zigbee network. This is what we will ultimately need to find. It is generated by the gateway, and shared by all the devices on the network. How does a new device join the network then? It uses the…
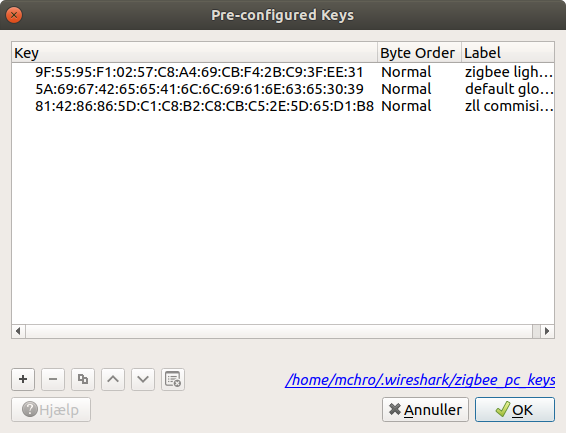
- The Key-Transport Key which is a pre-shared secret. Apparently there is a number of these, depending on the class of devices and type of network. These are apparently a well-kept secret or something, although widely available on the internet:
- “default global trust center link key” which is 5A:69:67:42:65:65:41:6C:6C:69:61:6E:63:65:30:39
- “light link master key” which is 9F:55:95:F1:02:57:C8:A4:69:CB:F4:2B:C9:3F:EE:31
- “light link commissioning key” which is 81:42:86:86:5D:C1:C8:B2:C8:CB:C5:2E:5D:65:D1:B8
You can add these keys to Wireshark, and the Zigbee dissector will then try to decrypt traffic using them. Go to Edit -> Preferences -> Protocols -> ZigBee and edit the pre-configured keys:
The Key-Transport Key is used whenever a new device joins the network with the sole purpose of encrypting the network key. So, to find the network key we need to know the Key-Transport Key, and observe the traffic when a device joins. So this is what I did: I found an IKEA Trådfri lightbulb and spent the frustrating time needed to get it to join the Philips Hue gateway (resetting the bulb, searching for new lights). Finally, it suceeded!
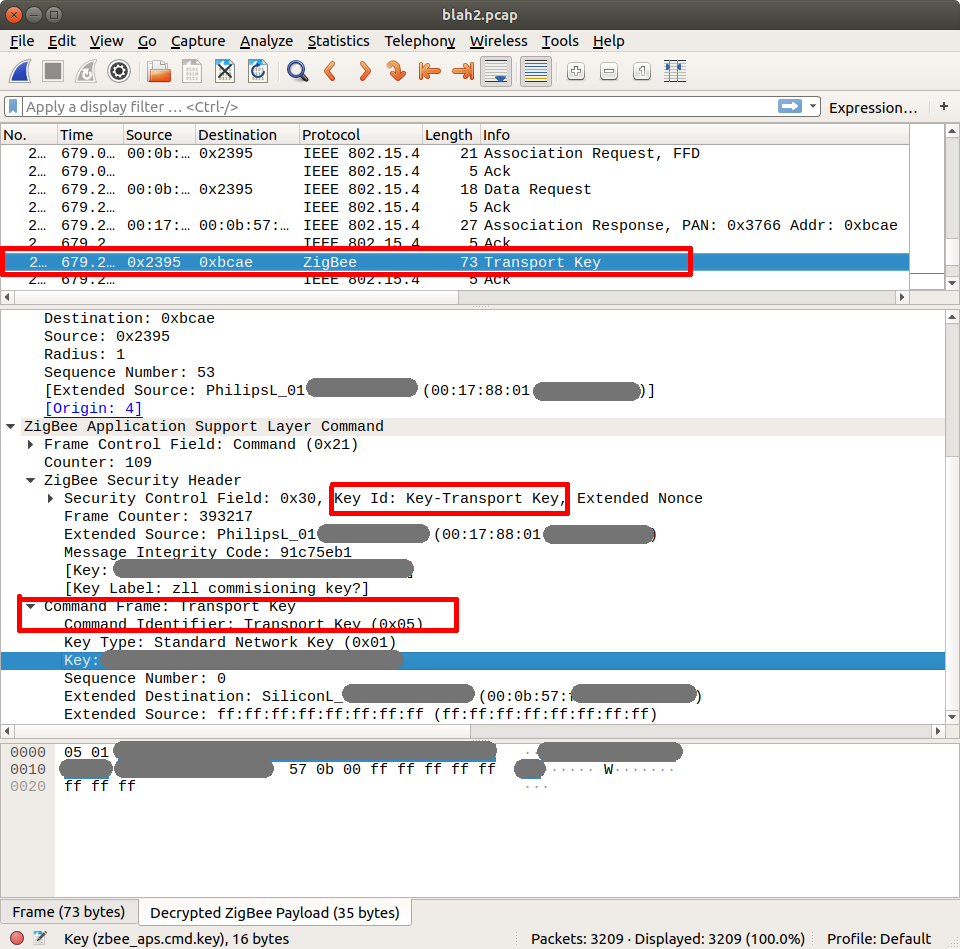
Now, by adding the transport key to the list of keys in Wireshark all the traffic on the network was able to be decrypted!
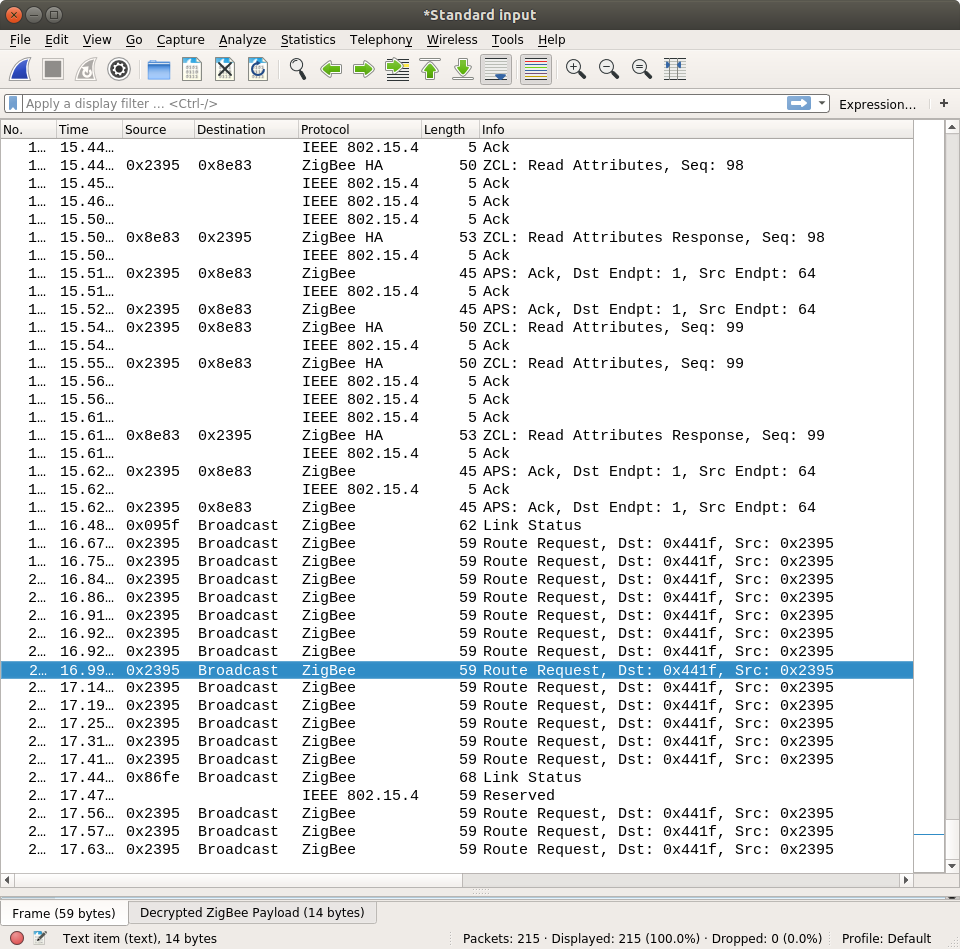
The next step will be to analyze the traffic, and understand the routing. Very initial probes using zigbee-viewer indicates that there is indeed three distinct routings:
So cool! I have started to dive into possibly sniffing through the Entertainment Area/Sync zigbee commands and your work is the closest I have seen to making sense of this traffic. Have you continued your research into this? Thank you for what you have put out so far!
Hi Nicholas,
unfortunately I never got any deeper than this, and my home Zigbee setup is currently in a minimally-working state.
/Mads